Updates
Since
the first blog post there have been considerable changes and progress to my
Capstone project. After working with DNS covert channel forensics, it became
clear that the project was too large to fully complete within four months. With
that realization I still wanted to have my new project focus around covert
channeling. I then found a program called Hping3 and decided to have my
capstone focus around finding artifacts on hping3 when used to send data via
cover channeling.
Once
I switched my project to hping3 I started researching the program and testing
its capabilities. Hping3 is a command
line based tool that can be used to troubleshoot and test networks and hosts.
In addition to its ability to test network connection and help a company, it
also has the capabilities to send information through different network
protocols. My tests done so far have been tested on IP, ICMP, and UDP.
The Research
The
first part of setting up to test this program was to create two separate VM
machines on two separate local machines. Both of these machines are running
Ubuntu 12.04.4. I then imaged them to create a control for comparison after
running hping3.
After the snapshot I then created sample data which consists
of three test documents, and they are located on the desktop. In
addition to that I downloaded hping3.
At this point all further steps moved to the command line
(Terminal). Below is the command to install hping3 from the desktop.
Sending Plain Text
Test 1
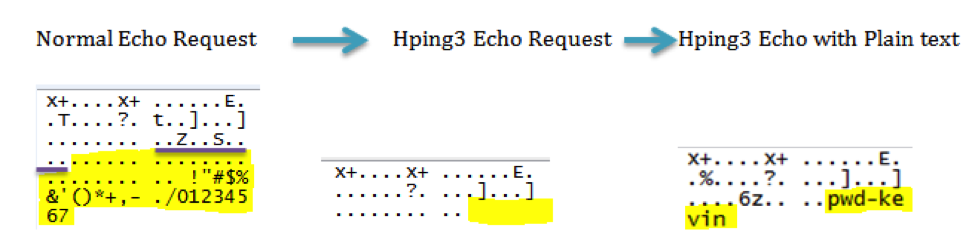
My first set of tests involved sending data though ICMP echo
requests. Here is a normal echo request that was captured using Wireshark.
The underlined blue is the size of the packet which is 84
bytes. The underlined purple is a timestamp for the data being sent across, and
the hex values bracketed within the red is the actual data being sent across.
Test 2
Below was an ICMP echo request sent using hping3. The packet
was captured using Wireshark.
The underlined hex values are resent that this packet is an
IP packet (08 00); it has a size of twenty-eight bytes (00 1C) the source (28
5d 93 c3) and destination IP (d8 5d 93 b8), and it contains the type of ICMP
packet send which is an echo request which is represented by the 08 00 in the
hex.
Test 3
Lastly I sent data though plain text using hping3. The
command I used was Sudo hping3 -1 216.93.147.184 –e
pwd-kevin.
The captured packet after being sent looked like this.
The underline green represents important changes to the
packet compared to the previous hping3 echo request. The first is the size of the packet. It went
from twenty-eight bytes to thirty seven. The added nine bytes are from the plain text
data pwd-kevin. The last nine bytes are the plain text data I entered into my
command.
The
primary differences noticed are the data strings. These are highlighted in
yellow. The other difference is that hping3 does not timestamp the data.
With
the time remaining to work on my project I am going to analyze an image of the
VM I have been working on to see what data is stored on the machine. After I
discover what is stored I will repeat the process for sending hex messages
through hping3 and also sending entire text documents through hping3.