This final blog post will summarize
my findings on my Capstone project on Hping3 forensics. Since my research
portion was finished in the last blog post this post will focus on obscuring
the data, catching the data using an intrusion detection system (IDS), and why this
information is significant.
Obscuring the Data
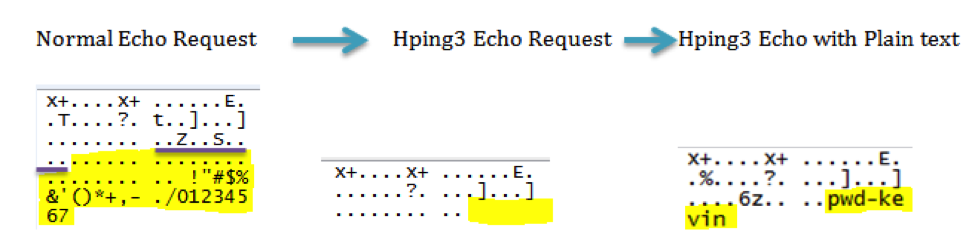
Hping3 has the ability to send
entire documents through ICMP packets. In order to better obscure this data there
are two ways that are ideal for data to sent over the network covertly. The first is
setting a specific amount of bytes of data per packet. The two sizes that would
be the lease suspicious would be one and forty-eight bytes. One byte would be
ideal because of the size of the packet. A small ICMP packet is not an unusual,
and would not raise suspicion. Forty-eight bytes on the other hand is the
normal size of data found in an ICMP echo request. By matching an echo request
size any IDS would not flag the packet based on
its size.
Below is command typed to send a
document (test) through to an IP address (216.93.147.70) at one byte at a time
(-d 1).
The second way to better obscure the data being sent out is through delaying each request. By delaying request with data in them it slowly sends data out rather than all at once. It would be harder to catch data being sent out over a day than it would be in thirty seconds.
Using
an IDS
In
order to protect information an IDS can be used to catch Hping3. During testing
Wireshark 1.10.2 was used not only to capture network packets, but also was used
as an IDS. The following parameters were created to help filter legitimate
packets from Hping3 packets.
The
first parameter was data =! 48. This would filter all packets that did not
equal forty-eight bytes. This would catch any packet data that was not a normal
ICMP packet. Although not all legitimate packets will be forty-eight bytes, it
is a good parameter to set for catching nefarious ICMP traffic.
The
second parameter is timestamp = present. This parameter will filter all traffic
with timestamps in their headers. Hping3 does not generate a timestamp when it
sends an ICMP packet. You use the time stamp parameter to find non-hping3
packets, and the remainder packets should be inspected closer.
These
two parameters together would help detect and catch Hping3 packets leaving or
entering a network both live, and as saved log files.
Significance
The
significance of my project had two primary goals. The first is to make people
more aware of the simplicity and ease of creating covert channels that can move important data
off of a network, and for companies to be aware of how the software works. The
other significant reason for this research would be helpful for investigators
to know where to look both on a local machine and on the network to find this
software or similar network exfiltration tool. Greater exposure on both where
to find artifacts, and how to use an IDS to catch use of this software could
save time, and money. These reasons are why this project is significant, and
hope that this information can help mitigate data theft.